Some Reversing/Misc Mix!
The hidden function
This binary politely greets you when you run it, no useful string with rabin2. Running it with r2 you'll see a very simple entry0 followed by a main, yet the binary is healthy, no hlt or bad jump whatsoever. Trying afl , gave an interesting list of functions, two of which was entry1.init and entry2.fini. Seeking to them and there was a jump just before a function epilogue. Looked for references for the function, i.e. 0x804841d, using axt [addr] and surprisingly nothing. This function as you see here seems to contain words and if you follow it at the end there is a loop followed by a printing function. Typical for a flag printer.
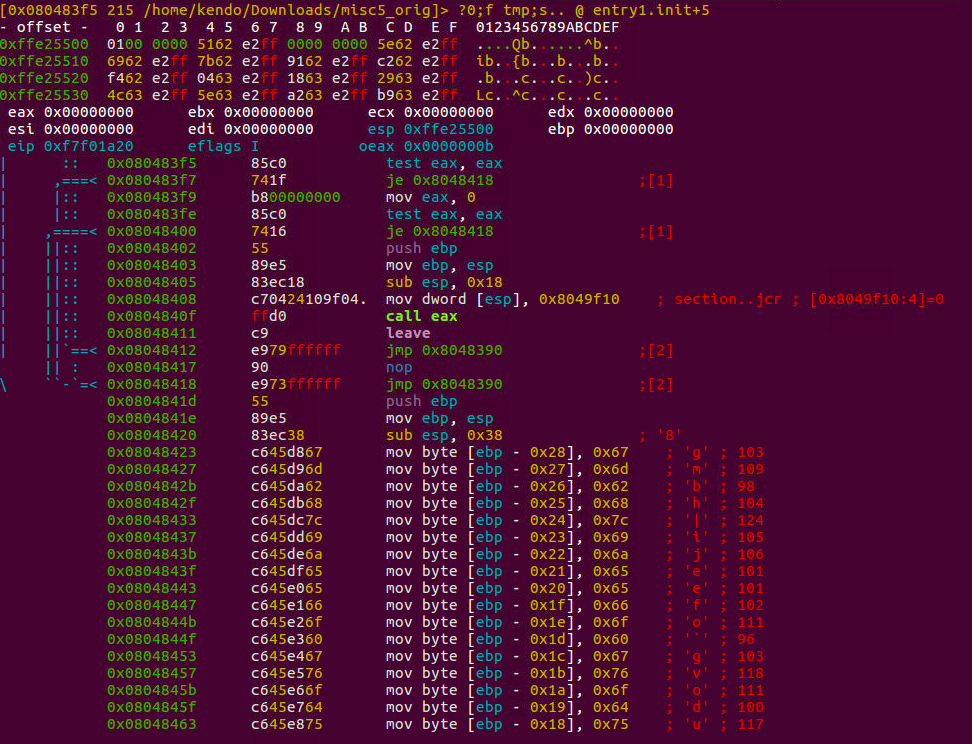
Patching the entry0 to go call this address instead of main, plotted the flag successfully.
Reversed Binary
A very interesting file about which rabin2 reveals some interesting strings:
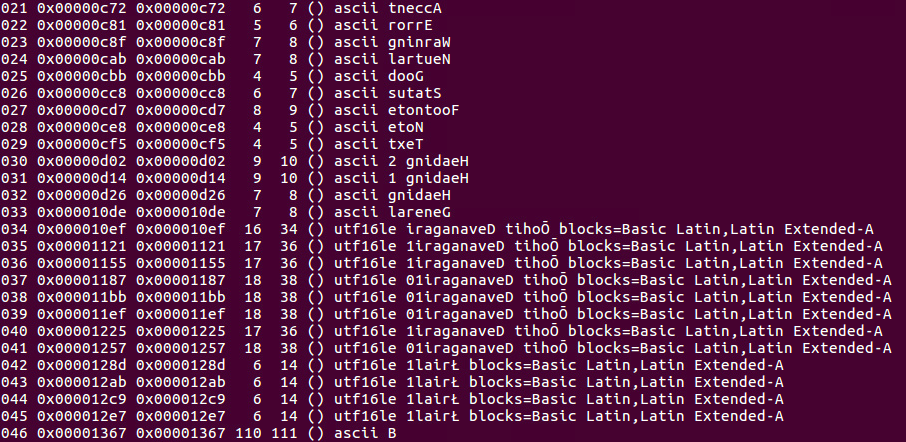
The words are mirrored: General, Heading, Note, Footenote, etc. Looking more around and I noticed it's actually an excel file, mirrored! As usual, probably there are better ways to do it, but this small script did the job:
with open("Misc", 'rb') as ff:
q = bytearray(ff.read())
q.reverse()
with open("Misc_mirror",'wb') as ff2:
ff2.write(q)
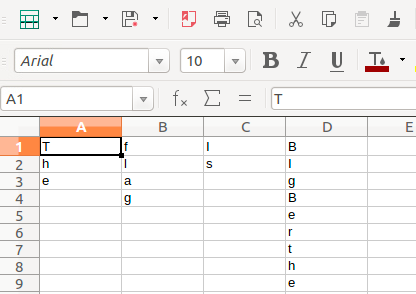
and then trying to open it with LibreOffice Calc revealed the flag:
Dialtone wav
This (misc) challenge gave us a very short wave file containing a dial tone. First, I naively tried to plot the frequency of the tone to find out the numbers based on their frequencies using the dial pad frequencies:
from scipy import signal
from scipy.io import wavfile
import matplotlib.pyplot as plt
q = wavfile.read("./Misc")
f, t, Sxx = signal.spectrogram(q[1], q[0])
plt.pcolormesh(t, f, Sxx)
plt.show()
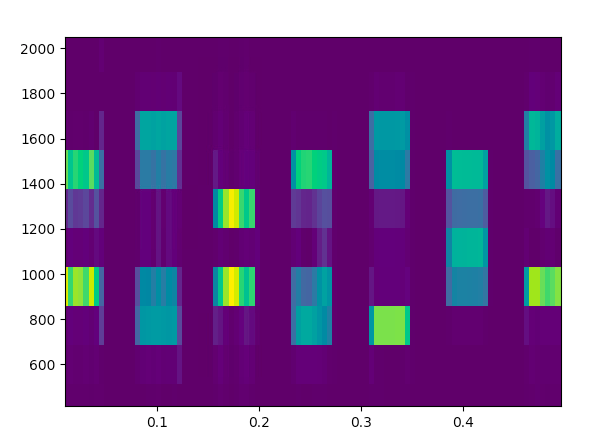
However, some of the tones spectrum were not making any sense. So, google came to help by introducing me to this very nice dtmf decoder:
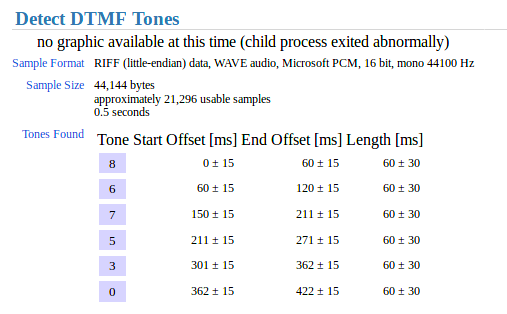
however that number didn't work as a flag, the song's number, however, did :D
